Visible to Intel only — GUID: uri1666025705860
Ixiasoft
Visible to Intel only — GUID: uri1666025705860
Ixiasoft
3.2.2.2. Memory Subsystem TCAM Operations
Insertion
To insert a new entry, a key and mask are needed. The key is first split into a number of chunks. If no bits are masked, then the slice value is used to address a single location and a single bit corresponding to the entry number is set to 1.
If any bits within this slice are set to don’t care (that is, if any bit in the mask is set to 0), then the same operation must be performed by the management logic for all possible values of the don’t care bits.)
Example: Consider the following key slice: 1001 and its corresponding mask value of 1011, which are associated with entry 1. The management logic sets bit number 1 (corresponding to entry 1) at the following addresses of the key RAM for this slice:
- 1001
- 1101
Delete
There are two forms of the delete operation:
- Entry-based – Takes the entry ID as the only argument and deletes an entry by clearing all corresponding bits in all locations of the key RAM for all possible slice values.
- Entry/key/mask-based – Uses information about which slice memory locations must be accessed, based on the key and mask information, and clears only the bits which have previously been set. This generally reduces the time required to delete an entry by reducing the number of memory writes required.
Lookup
Lookup operations can occur as a result of a request from external logic via the AXI ST lookup request interface, or as a result of a management operation initiated by the CPU through the AXI-Lite control register interfaces. The system multiplexes requests from these two sources and sends them through a common pipeline. Internal metadata is used to de-multiplex the lookup results to either the lookup response output or the management block. External lookup requests have higher priority than any management operation.
In the lookup process, the key is divided into slices and each slice is used to address a corresponding memory location in the key RAM. A data word from each RAM slice indicates which entries the corresponding slice value matches.
An AND operation is then applied to the data words from each slice location and the resulting vector indicates the entry matches for all slices of the key.
The core compares the search key against every valid entry in its database, where a key bit is compared only if the entry’s corresponding mask bit is set to 1. This means that an entry with a mask of all zeros will always match every search key; however, because several entries may provide a match, the response only outputs the highest matching entry ID.
Example
The following diagram shows the state of the Key RAM after inserting 5 entries.
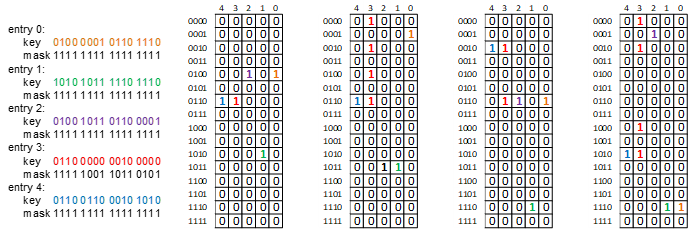
Entries 0, 1, 2 and 4 are expected to match exactly. Entry number 3 has several bits masked out (that is, marked as don’t care by setting the corresponding bit positions to 0.
The following two searches are performed, to illustrate the principle of operation:
Example 1: Lookup key 1010 1011 1110 1110
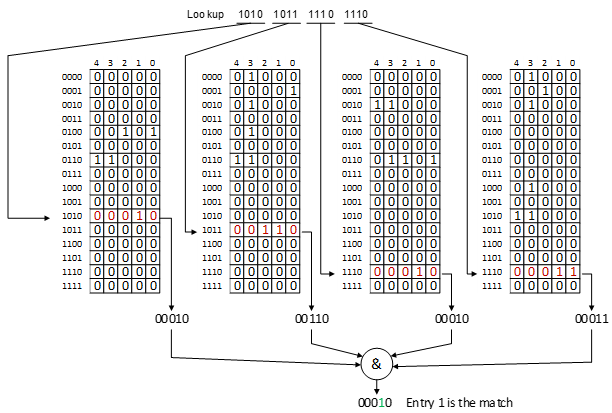
In the above example, there is only one matching entry (entry number 1) and it is an exact match.
Example 2: Lookup key 0110 0110 0010 1010
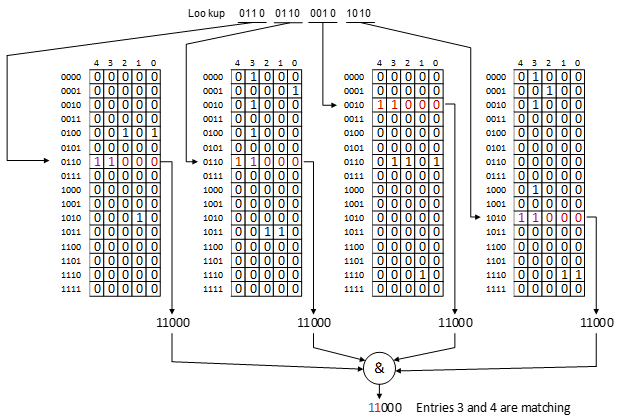
There are two matching entries – entry number 4, which is an exact match, and entry 3, due to its masked bits. If the MS-TCAM is parametrized to operate in standard TCAM mode where the highest matching entry is selected as the output response (GEN_PRIO_RESP = 1), then entry 4 is selected as the matching entry and its entry number appears at the output (along with optional result field). Otherwise, the match vector showing the two matching entries appears as the lookup response.