Quartus® Prime Pro Edition User Guide: Design Compilation
Visible to Intel only — GUID: irb1721259922051
Ixiasoft
Visible to Intel only — GUID: irb1721259922051
Ixiasoft
1.16.4.1.4. SDC-on RTL Example: Applying Constraints at Deeper Hierarchies
Within your design, you can apply constraints at different levels of hierarchy using the pipe character (|) to separate hierarchy levels of instances. Constraints are applied when the hierarchy levels match and the string values, including wildcards, match the pin names. For example:
get_pins U3|U0_lv1|U0_lv2|U0_lv3|flag
The fundamental timing analysis flow requires executing the fitter to elaborate the timing netlist before applying any constraints. In the following example, suppose you intend to constraint a generated clock buried deep within module A:
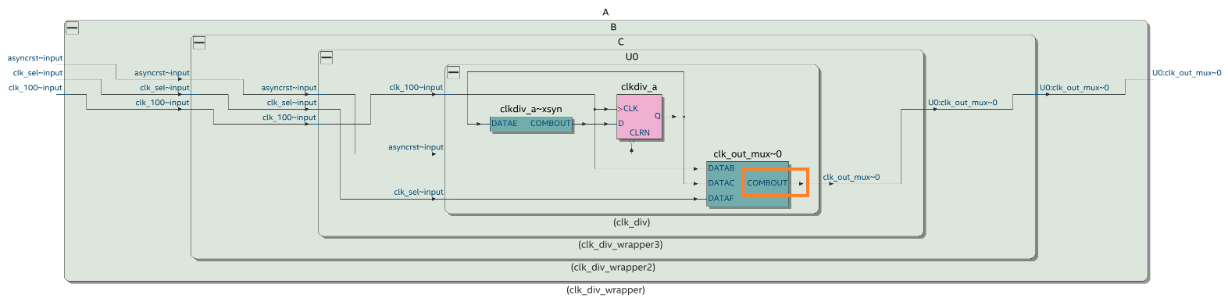
To achieve this, locate the cell clk_out_mux where the constraint must be applied and identify the pin name COMBOUT. This process often results in a complex path name that can be challenging to decipher, especially when module names are intricate (unlike straightforward names, such as A|B|C). Additionally, suppose the hierarchy evolves in the future. In that case, you must rerun the fitter and delve into the design again to derive the updated path, which can lead to inconsistencies between the design and the constraint targets. You can target the COMBOUT pin as follows:
get_pins A|B|C|U0|clk_out_mux~0|combout
SDC-on-RTL also offers an efficient means of constraint propagation, enabling you to apply constraints at module boundaries. It ensures that these constraints seamlessly extend to the corresponding leaf instances during the synthesis stage. For instance, revisit the previous example, in which the clock constraint embedded within module A can be established using SDC-on-RTL constraints at the module A's boundaries, specifically focusing on the clk_out pin.
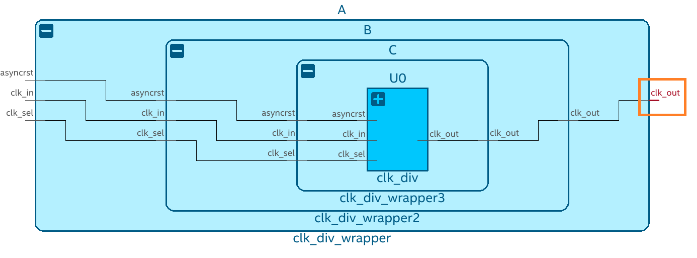
To target the clk_out pin of module A, use the following filter:
get_pins A|clk_out
By directing your attention towards pins located at the boundaries of abstract blocks, you gain the flexibility to modify the internal instance hierarchy as needed. Constraints remain effective even if you decide to rename an internal instance within your module, for instance, changing it from A|B|C|U0 to A|X|Y|U0. Importantly, this can be accomplished without requiring alterations to your existing constraints. This demonstrates the robust capabilities of SDC-on-RTL, allowing you to concentrate on boundary pins rather than navigating complex hierarchies. This approach ensures constraint accuracy and simplifies constraint management.
After creating the constraints, rerun the Analysis & Elaboration on the Compilation Dashboard to apply the constraints to your design. Open the Constrained checkpoint of the RTL Analyzer and carefully select the nodes where the constraints were applied. Utilize the Property Viewer to verify the correct application of constraints to these nodes. For additional information, refer to Inspecting SDC-on-RTL Constraints.
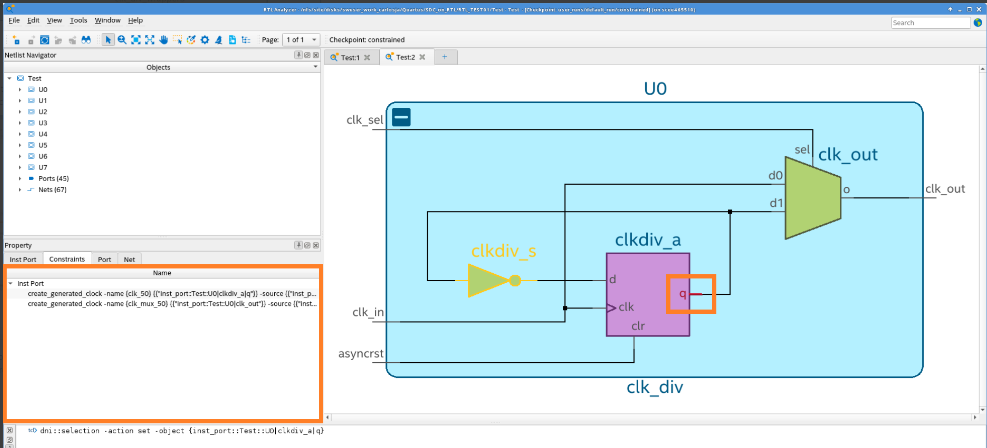
Utilize the Quartus® Prime software's additional tools to explore and confirm that all SDC constraints were read and successfully applied. Tools like the Constraints viewer launched from the RTL Analyzer can assist you in verifying and cross-probing the constraints with the Schematic Viewer.
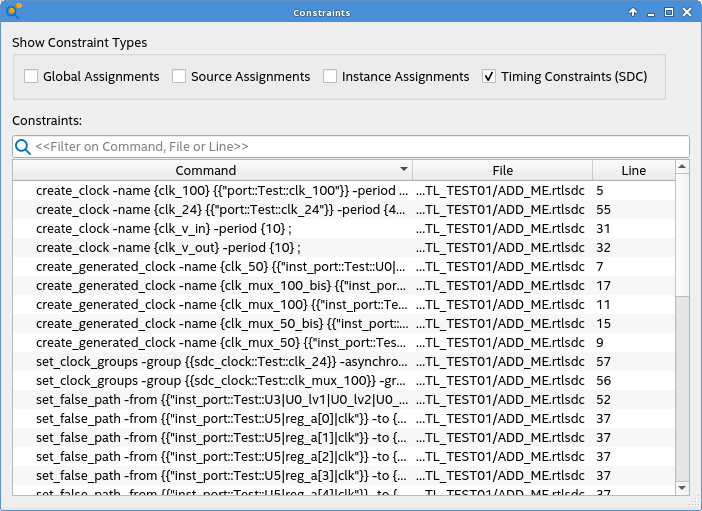
Additionally, the reports under Compilation Report > SDC Constraints folder provide a detailed view of the constraints and their locations. Use the Constraint Propagation Report to view how constraints are propagated as the netlist is transformed and inspect where the constraints end up post optimizations.