Visible to Intel only — GUID: sca1672959218342
Ixiasoft
2.1. System Architecture
2.2. Data Path Between Ethernet MAC and MACsec
2.3. Data Path Between MACsec and MCDMA
2.4. Data Path Between MACsec and Packet Generator/Checker (Packet Client)
2.5. Data Path Illustrations
2.6. Interrupts
2.7. Packet FIFO
2.8. AXI-ST Rate Controller
2.9. Error Handling
2.10. Top Level Signals
6.5.1.1. MACsec Reset Sequence
6.5.1.2. TX Configuration Sequence
6.5.1.3. RX Configuration Sequence
6.5.1.4. TX Rekeying Sequence
6.5.1.5. RX Rekeying Sequence
6.5.1.6. Cut Through/Store Forward Mode
6.5.1.7. User Single/Multi Port Settings
6.5.1.8. Encrypt/Decrypt Port
6.5.1.9. Port Priority
6.5.1.10. Interrupt Generation and Register
6.6.1. macsec_initilize
6.6.2. macsec_get_attributes
6.6.3. macsec_get_sa_attributes
6.6.4. macsec_set_attributes
6.6.5. macsec_set_sa_attributes
6.6.6. macsec_read_register
6.6.7. macsec_write_register
6.6.8. macsec_set_port_configuration
6.6.9. macsec_rate_configuration
6.6.10. macsec_single_or_multi_port
6.6.11. macsec_crypto_mode
6.6.12. macsec_port_priority
6.6.13. macsec_register_isr
7.1. Software Requirements
7.2. Obtaining the Reference Design
7.3. Reference Design Directory Structure
7.4. Simulation Command Arguments
7.5. Simulation Test Cases
7.6. Complete Simulation Command
7.7. Simulation Requirements
7.8. Running Non-UVM Simulation
7.9. Running UVM Simulation
7.10. Building, Installing, and Running the Software
7.11. Building the Hardware Design
Visible to Intel only — GUID: sca1672959218342
Ixiasoft
2.2.1.3. Order of Ethernet Transmission
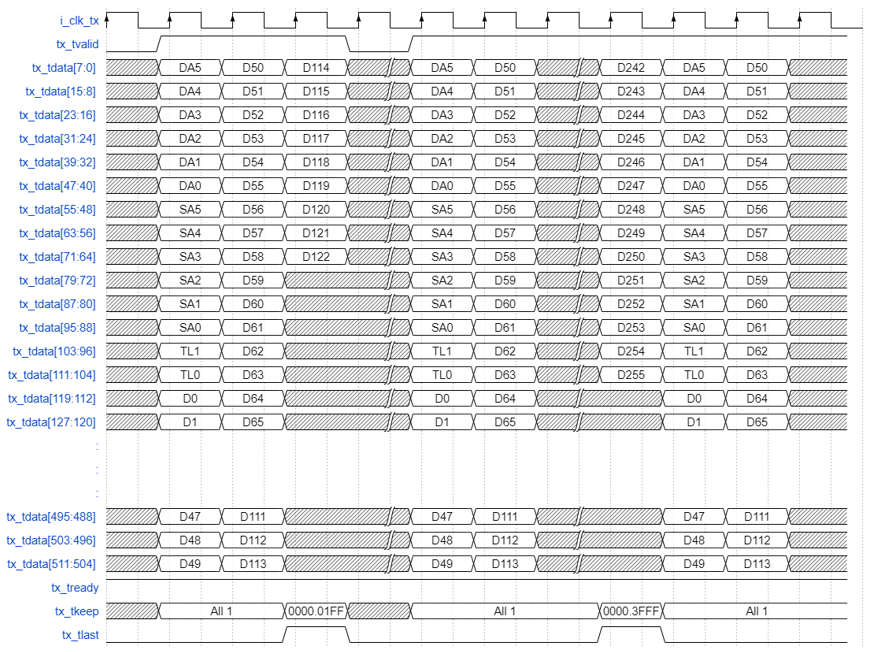
The TX MAC transmits bytes on the Ethernet link starting with the preamble and ending with the FCS in accordance with the IEEE 802.3 standard. On the transmit client interface, the IP core expects the client to send the most significant bytes of the frame first, and to send each byte in big-endian format. Similarly, on the receive client interface, the IP core sends the client the most significant bytes of the frame first, and orders each byte in big-endian format. Whereas the MACsec IP sends and expects frames to be in least significant bytes first and each byte in little-endian format. The AVST-AXI-ST bridge handles this ordering between the MACsec and E/F-tile IP.
Figure 9. Ethernet Frame Octets
For example, the destination MAC address includes the following six octets AC-DE-48-00-00-80. The first octet transmitted (octet 0 of the MAC address described in the 802.3 standard) is AC and the last octet transmitted (octet 7 of the MAC address) is 80. The first bit transmitted is the low-order bit of AC, a zero. The last bit transmitted is the high order bit of 80, a one. The following figure shows that in this example, 0xAC(DA5) is driven on [511:504] in case of AVST and on[7:0] in case of AXI-ST and 0x80(DA0)is driven on [471:464] in case of AVST and on [47:40] in case of AXI-ST.
Figure 10. E/F-tile AVST Interface for 100G
Figure 11. MACsec AXI-ST Interface for 100G