Vulnerability Handling Process
Intel PSIRT Process: Identify, Mitigate, Disclose
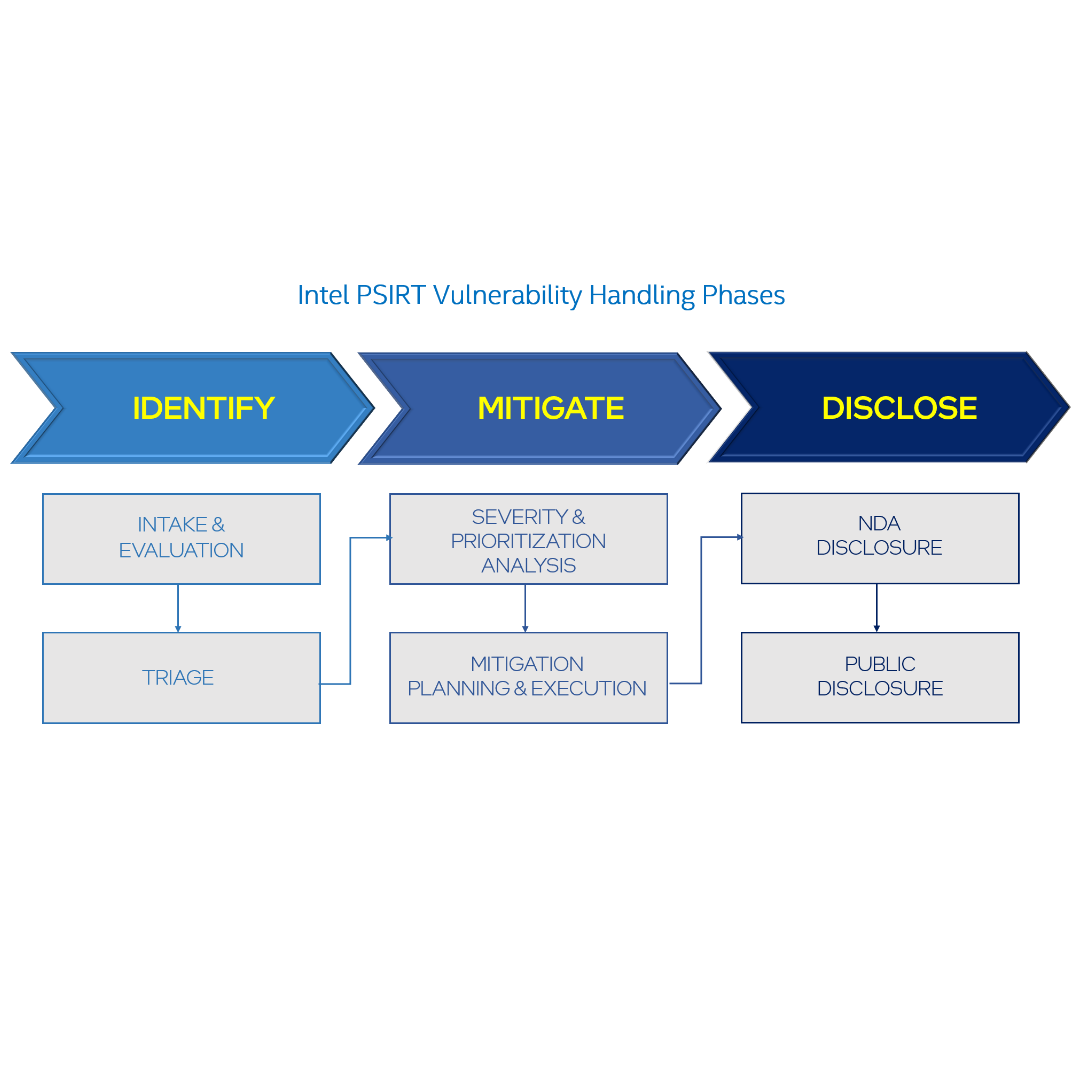
The Intel PSIRT outlines comprehensive and repeatable processes for how issues are addressed within the company. For example, potential security vulnerabilities are prioritized based on severity and impact, with handling done in three phases: Identify, Mitigate, and Disclose.
PSIRT receives potential vulnerabilities from internal or external vulnerability reporters and works within Intel to verify the reported information through two steps:
Intake
Intel PSIRT evaluates initial potential vulnerability information and requests additional details, as needed, to properly disposition the issue.
Triage
PSIRT works with product teams to evaluate and reproduce the report, and to understand the potential impacts to products.
- If a potential vulnerability can be reproduced, then the Intel PSIRT executes the remaining PSIRT process through public disclosure.
- If a vulnerability can’t be reproduced or it’s found not to affect an Intel product, then the Intel PSIRT relays this information to the vulnerability reporter and closes the case.
Intel aims to help protect the broader technology ecosystem by partnering with industry security researchers to share information about reported security vulnerabilities with our customers, competitors, and fellow technology vendors in a timely fashion. Following CVD practices, if Intel recognizes that another vendor’s product might be affected by a reported vulnerability, we coordinate with potentially affected vendors, relevant third-party coordinators, and/or vulnerability reporters, depending on the vulnerability report.
This association with industry vendors is seen as reciprocal. Intel asks that our partners follow a similar strategy to share reported vulnerabilities with the ecosystem.
PSIRT finalizes severity and prioritization for vulnerabilities using metrics such as Common Vulnerability Scoring System (CVSS). Alongside severity and prioritization analysis, Intel works to evaluate strategies to mitigate the vulnerabilities and execute on the determined strategy.
Severity and Prioritization Analysis
Intel uses the most up-to-date version of CVSS, an industry framework maintained by the Forum of Incident Response and Security Teams (FIRST). CVSS captures the intrinsic, technical characteristics of a vulnerability to determine its severity.
CVSS scores range from 0 (lowest severity) to 10.0 (most critical severity). CVSS is broken down into three metric groups – Base, Temporal, and Environmental. Intel only uses the Base Metrics to score vulnerabilities, which is referred to as the “Base Score.” Intel only publishes the CVSS Base Score at this time. CVSS uses the Severity Categories and Base Scores as shown below:
NOTE: CVSS is not a risk calculation methodology. CVSS only captures a vulnerability severity rating, which could be used as an input to risk calculations.
We encourage customers and users to evaluate the impact of a security vulnerability in their specific environments, as many factors determine a vulnerability response prioritization decision.
Mitigation Planning and Execution
Intel develops and implements a mitigation plan or solution to address the identified security vulnerability. Intel works diligently to identify mitigations in a timely manner. Response timelines vary based on the complexity of the issue, number of products affected, priority, and product release cycle (if applicable), among other factors.
PSIRT communicates the appropriate vulnerability information and any associated mitigations to our customers and the public following a tiered approach to disclosure. This allows partner organizations time to test, verify, and implement mitigations before coordinated public disclosure.
NDA Disclosure
Intel informs customers at appropriate times, based on the degree to which they’re involved in the mitigation of a security vulnerability. Partners that need to assist in development of the mitigation are informed via NDA at the earliest appropriate time after Triage.
Public Disclosure
PSIRT publishes public vulnerability disclosures in the form of Security Advisories once NDA disclosure is complete. PSIRT balances the need to provide actionable information with seeking to prevent attackers from operationalizing vulnerability information. The full list of Security Advisories can be found on the Intel Product Security Center.
Our Security Advisories contain the following information:
- A summary of the vulnerability
- Vulnerability details including CVE identifier and CVSS information (Base metrics only)
- Affected products and versions
- Recommendations for customers to include mitigation information or other actions required by the customer
- Acknowledgements to the vulnerability reporter or third-party coordinator (Intel acknowledges the reporter with their permission during public disclosure)
We are a CVE Numbering Authority (CNA) and assigns Intel CVEs for public vulnerability disclosure. Intel Security Advisories contain CVE, CVSS, and mitigation information for customer use.
PSIRT won’t provide additional vulnerability details beyond what is published in a Security Advisory to ensure appropriate data protection. When a Security Advisory requires further explanation, Intel works with ecosystem partners to generate a technical paper to give guidance, tips and/or supplemental development information.
Learnings from these issues and feedback from the ecosystem will be incorporated in the next development cycle.
Disclosure Schedule
PSIRT publishes Security Advisories on the second Tuesday of the month. In some circumstances, Intel PSIRT may publish outside of this schedule based on a variety of factors.
Intel manages all sensitive information in a secure manner. Vulnerability information is shared on a strict need-to-know basis. The Intel PSIRT asks that external vulnerability reporters maintain the same level of confidentiality while working with us through the PSIRT process.