Intel® Unique Platform ID Overview
The Intel® Unique Platform ID (Intel® UPID) is a globally unique and persistent identity that can be used to identify a platform throughout its lifecycle. The Intel UPID is equipped with an IDevID (Initial Device Identifier) private key that is protected by the Intel® CSME security engine and an IDevID certificate issued by the Intel certificate authority. The certificate adheres to the IEEE 802_1AR 2018 industry standard for IDevID certificates.
The Intel UPID can be used to challenge (and verify) a client endpoint’s identity for various purposes. The Intel UPID IDevID certificate is issued by the Intel® CSME On Die Certificate Authority (Intel® ODCA) infrastructure. The Intel CSME Firmware UPID application provides a host API that allows an application with admin level privileges in the OS or BIOS to challenge the Intel® CSME firmware to obtain a signed proof of the identity of the PC on which the application is executing.
This Intel UPID guide can assist application developers in incorporating use of the Intel UPID attestation in their applications.
Intel UPID Advantages
- The Intel UPID does not change, and cannot be changed, throughout the device lifecycle.
- The Intel UPID cannot be spoofed. Its integrity is protected, and it cannot be overwritten.
- The Intel UPID can be updated when a platform is refurbished.
- The Intel UPID is attestable by the Intel CSME.
Privacy Controls
The following features are included to satisfy privacy concerns:
- The user application interface requires OS administrator privileges to access the Intel CSME API that returns the Intel UPID, its IDevID certificate, and the certificate chain, and to access the Intel UPID Attestation API.
- An Intel CSME API is provided to allow the BIOS to control OS access to the Intel UPID APIs.
- The Intel UPID feature state controls access to the Intel UPID APIs. When the Intel UPID feature state is disabled, access to Intel UPID APIs that read the UPID or attest the UPID is blocked.
Intel UPID Usage Examples
Following are some examples of uses for the Intel UPID IDevID:
- Verifying a device’s identity when it is returned by the customer. The UPID_PLATFORM_ID_GET command can be used to read the device’s Intel UPID in the factory before the device is shipped. When a customer returns the device for servicing, or when a customer attempts to access a service specific to the device, the same APIs can be used to verify that the same device is being returned or is accessing the service.
- Using the Intel UPID when onboarding a device. The OEM can deliver a list of the device Intel UPIDs to the purchaser of the devices (for example, to an IT department that has purchased many devices). The purchaser can then use this list when an end-user attempts to onboard the device, to ensure that the device being onboarded is indeed the same one that the customer ordered.
- Disabling Intel UPID when it is not needed, to prevent unauthorized tracking of the device by OS-level applications. The OEM can implement a mechanism in the BIOS to prevent the OS from enabling the Intel UPID. The BIOS must enable reading Intel UPID to allow the OS to read it. If the BIOS has not disabled the Intel UPID, software with OS admin privileges can use the UPID_PLATFORM_ID_FEATURE_STATE_SET command to enable it and can read it. It is recommended for the OS to disable Intel UPID (by using the same command UPID_PLATFORM_ID_FEATURE_STATE_SET), so that if in the future the level of privilege needed to read Intel UPID differs from the level required to enable it, the customer has the option of disabling so that applications without Administrator privileges cannot access it.
- Attesting the device’s Identity as an additional factor for zero-trust access to corporate services and resources. The enterprise can collect the Intel UPIDs of the devices that it owns and can map each Intel UPID to the employee using the device. When a user attempts to access a corporate service or resource, the policy can ensure that the user can access it only from their approved device. To attest the device’s identity, the UPID_OEM_PLATFORM_ID_SIGN command is invoked.
System Requirements
Intel UPID is supported on 11th Generation (Tiger Lake) Intel vPro® or Intel vPro® Essentials devices and later programs.
The availability of the Intel UPID feature depends on the OEM enabling the support in the platform hence it may not be available for all platforms of these generations.
(See Detecting Whether Intel UPID is Supported on the Platform.)
The following table lists the programs that support Intel UPID, and the Intel CSME versions that also support device attestation:
| Platform | InteI CSME Firmware Versions Supporting Device Attestation |
|---|---|
| Tiger Lake | 15.0.42.X and later |
| Eagle Stream | 15.20.5.X and later |
| Alder Lake | 16.1.25.X and later |
| Fish Hawk Falls | 16.10.5.X and later |
| Raptor Lake and later | All |
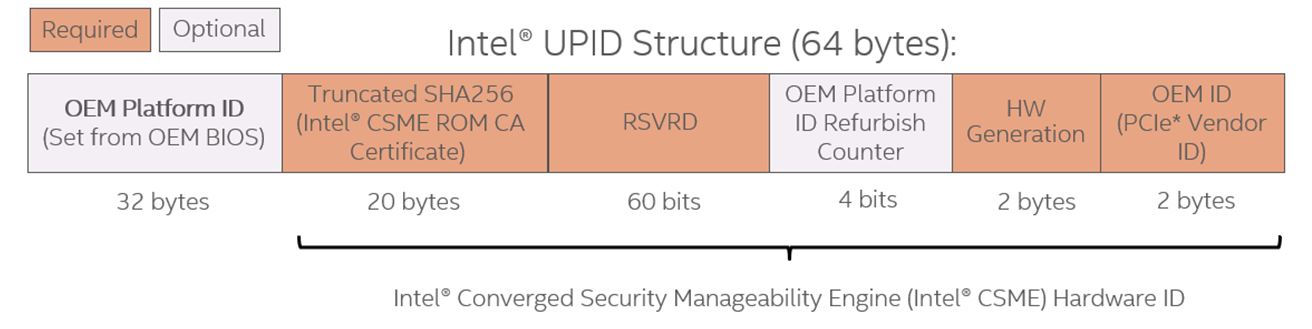
Intel UPID Structure
Following is the structure of the Intel UPID:
|
Field
|
Description
|
Comments
|
||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| OEM Platform ID | 32 bytes. Can optionally be set by the OEM BIOS before End of Manufacturing |
Stored in Non-Volatile Memory protected by Intel CSME | ||||||||||||||||||||||||||||||||||
| Truncated SHA256 | Truncated SHA256 of Intel CSME ROM On-Die-CA certificate provisioned to the Intel CSME fuses at Intel factory |
|||||||||||||||||||||||||||||||||||
| RSVRD | ||||||||||||||||||||||||||||||||||||
| OEM Platform ID Refurbish Counter | Can be incremented by the OEM BIOS when the device is refurbished. Stored in Intel CSME FPFs |
|||||||||||||||||||||||||||||||||||
| HW Generation | Initialized by the Intel CSME firmware |
Identifies the platform generation. Read from
|
||||||||||||||||||||||||||||||||||
|
OEM ID |
The vendor ID allocated by PCI-SIG |
Set by the manufacturer in the Intel CSME |
Intel CSME On Die CA
During Intel manufacturing, the Intel chipset is provisioned with a Certificate Authority certificate issued by the Intel Key Generation Facility (iKGF). This enables an on-die CA (Intel® ODCA) on the Intel platform to issue certificates for individual Intel CSME applications. The Intel ODCA issues the Intel UPID certificate, enabling Intel UPID Attestation. The Intel UPID certificate is issued following IEEE 802.1AR for an IDevID (initial device identity) certificate.
The following diagrams describe the Intel ODCA infrastructure in the Intel CSME firmware on different platforms.
When Intel UPID is enabled, the certificate includes the Intel UPID in alignment with the 802.1AR defined IDevID Certificate.
The ODCA TLS-Server certificate is used for the provisioning flow.
Certificate Chain for Tiger Lake and Alder Lake Platforms:
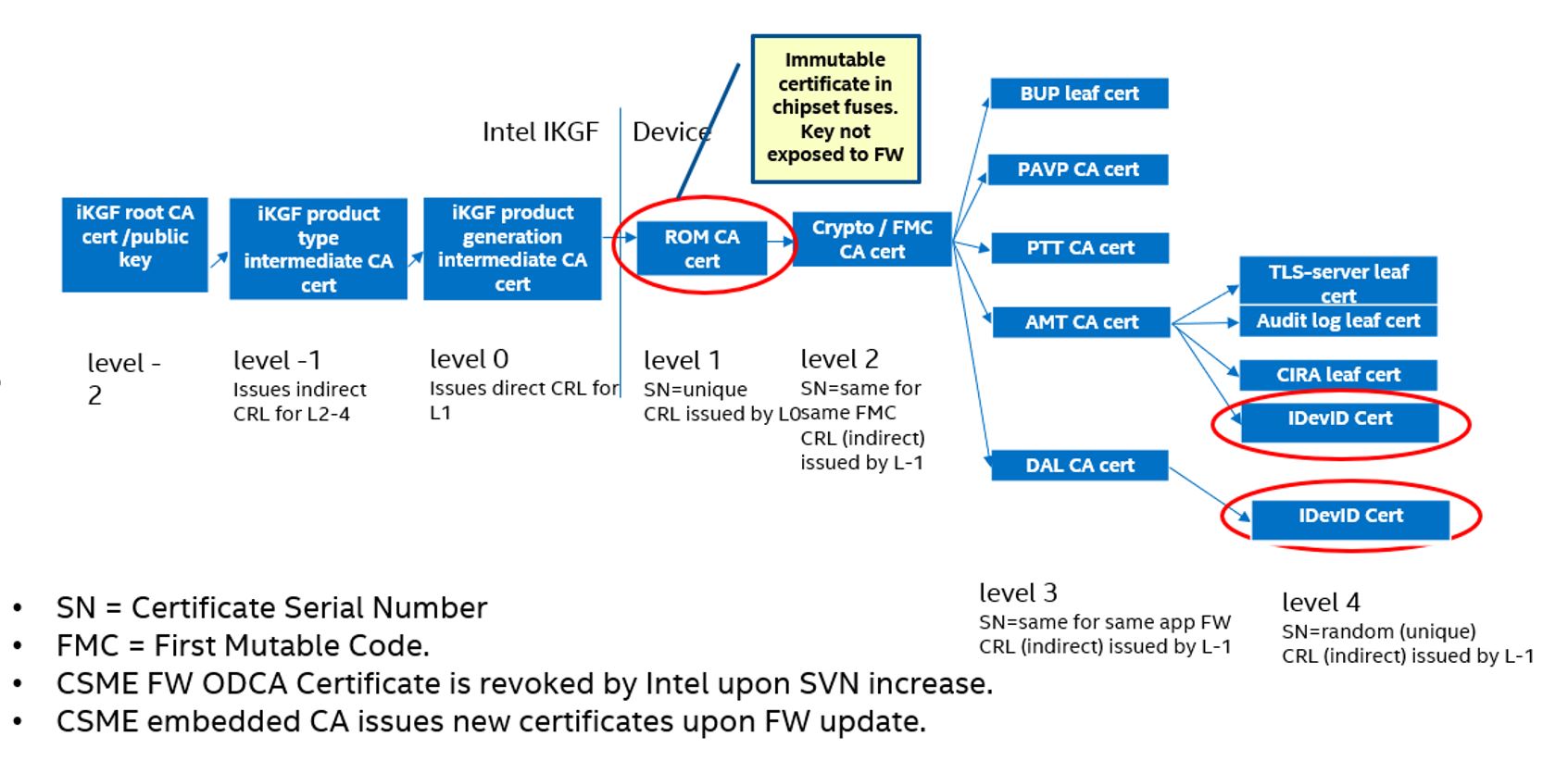
Certificate Chain for Raptor Lake and Later Platforms:
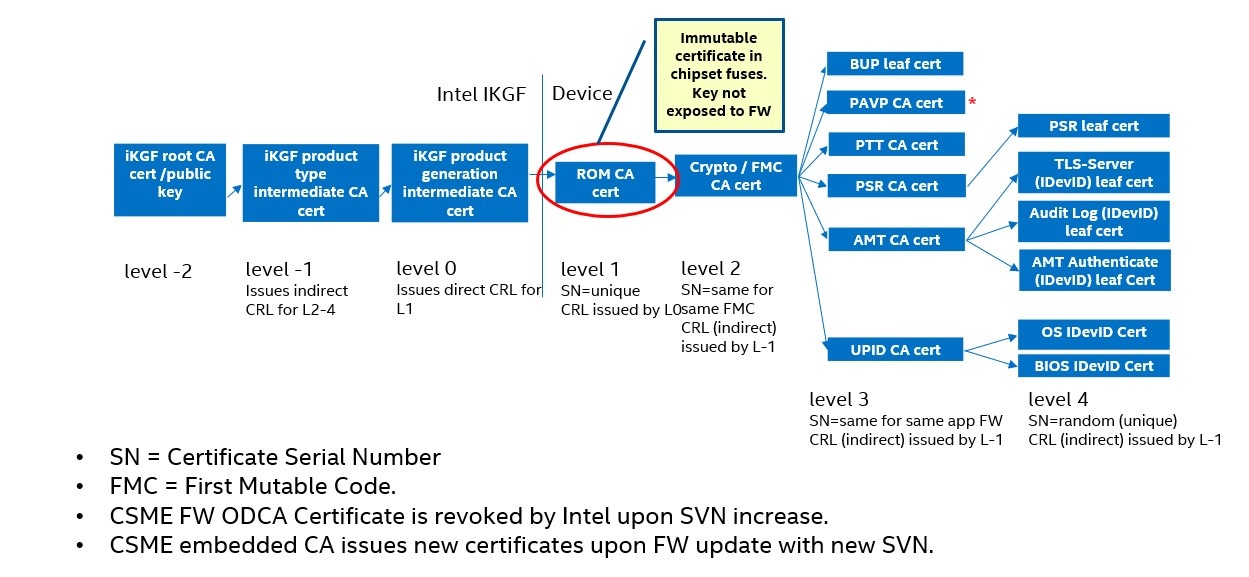
* Starting from Meteor Lake, the chain no longer includes the PAVP CA certificate.
The Intel CSME application key generation includes the following:
- the Intel CSME application’s Security Version Number (SVN)
- the application’s module ID
The Intel CSME certificate is revoked by Intel iKGF when the application’s SVN is incremented. Intel iKGF publishes the revoked certificates in a CRL (Certificate Revocation List).
Intel UPID IDevID Certificate Attributes
The platform uses the IDevID certificate to attest Intel UPID.
For definitions of the UPID OEM_ID, OEM Platform ID and CSME HW ID, see the table in Intel® UPID Structure above.
The certificate complies with the IEEE 802.1AR IDevID 2018 certificate standard and includes the following attributes:
|
Field
|
Value
|
|
|---|---|---|
|
Subject |
X520SerialNumber (OID = 2.5.4.5): |
< OEM Platform ID > in Hex char string format. Stored in protected Intel CSME non-volatile memory |
|
X520OrganizationName (OID = 2.5.4.10) |
<OEM_ID> OEM PCIe Vendor ID in Intel CSME fuses |
|
|
CommonName |
For Intel UPID Certificate: ” CSME IDevID OS /BIOS” |
|
|
subjectAltName (RFC4108) |
(OID = 1.3.6.1.5.5.7.8.4) HardwareModuleName ::= SEQUENCE { hwType OBJECT IDENTIFIER hwSerialNum OCTET STRING } |
hwType OBJECT IDENTIFIER: 2.16.840.1.113741.1.5.3.6.1 indicates that this is an Intel CSME UPID ODCA Hardware ID hwSerialNum OCTET STRING = the “<CSME HW ID>” |
|
Extended Key Usage |
X.509 V3 Extension |
2.16.840.1.113741.1.2.4.6 – for BIOS Intel UPID attestation 2.16.840.1.113741.1.2.4.7 – for OS Intel UPID attestation |
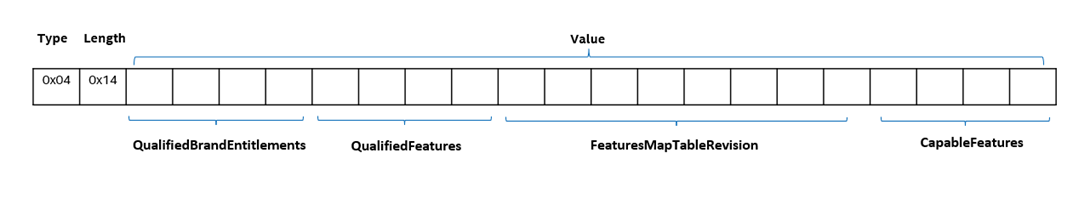
| Intel Brand Identity Extension | X.509 V3 Extension |
2.16.840.1.113741.1.2.5.1 Structure:
Qualified Brand and Entitlements: 4 bytes. Each bit represents a different entitlement. A value of 1 indicates that the entitlement is included. Field structure: Bit 0: Intel® Connectivity Performance Suite Bit 1: Intel vPro® Enterprise Brand Bit 2: Intel vPro® Essentials Brand Bit 3: Reserved Bit 4: Intel® Based PC Brand / For workstation: Intel® Xeon® Based Workstation (when Brand Features Map Table Revision is 19.10.x.x) Bits 5-30: Reserved Bit 31: Intel® Connection Manager Entitlement
Intel CSME Brand Qualified Features: 4 bytes. Each bit represents a different Intel CSME feature. A value of 1 indicates that the feature is qualified. Note: Some features are mandatory - they must be enabled by the OEM. Other features are optional. Whether a feature is mandatory or optional depends on the platform. To discover which features are mandatory and which are optional for your platform, refer to the Intel® Unique Platform ID landing page. Bit 0: Intel® AMT Bit 1: Intel® Standard Manageability Bit 2: Reserved Bit 3: Intel® One-Click Recovery Bit 4: Intel® Remote Platform Erase Bit 5: Intel® Platform Service Record Bits 6-17: Reserved Bit 18: Out of Band KVM Remote Control Bits 19-26: Reserved Bit 27: Out of Band Over ThunderboltTM Dock Bit 28: Intel® Unique Platform ID Bit 31: Reserved
Brand Features Map Table Revision: 8 bytes Bytes 0-1: Major version of Intel CSME firmware Bytes 2-3: Minor version of Intel CSME firmware Bytes 4-5: Hot fix number of Intel CSME firmware Bytes 6-7: Build number (version of the map table – across generations)
CPU Brand Qualified Features: 4 bytes. Each bit represents a different CPU feature. A value of 1 indicates that the feature is qualified. Bit 0: Intel® System Security Report Bit 1: Intel® Runtime BIOS Resilience L2 Bit 2: Intel® System Resources Defense Bit 3: NVMe Based Firmware Recovery Bits 4-31: Reserved
Extension: = SEQUENCE {2 elm OBJECT IDENTIFIER 2.16.840.1.113741.1.2.5.1, OCTET STRING OCTET STRING [Qualified Brand and Entitlements || CSME Brand QualifiedFeatures || Brand Features Map Table Revision || CPU Brand Qualified Features] } where || stands for concatenation of the values above. |
Intel UPID MEI Commands
Intel UPID MEI Client Definition
GUID = 92136C79-5FEA-4CFD-980E-23BE07FA5E9F
TxBufferSize = 1200 bytes
RxBufferSize = 3,500 bytes
MaxClients = 1
Detecting Whether Intel UPID is Supported on the Platform
A platform’s Intel UPID capability can be detected from the presence of the Intel UPID MEI client in the Intel CSME firmware. When the Intel UPID MEI client is present, it registers its GUID with the Intel MEI driver.
The Intel MEI driver provides an interface through which software can query the list of HECI Client GUIDs supported by the Intel CSME firmware and thereby discover whether the Intel UPID MEI Client GUID is on the list. Once the Intel UPID MEI Client GUID has been found, it is also possible to discover the version of the Intel UPID feature.
If Intel UPID is not supported on the platform, the OEM should be contacted to enable the feature.
To query the Intel MEI driver for the supported Intel MEI Client GUIDs and GUID versions:
- Use the GetDevicePath function to retrieve the Intel MEI driver filename via GUID.
- Open a handle to the Intel MEI driver (via CreateFile, using the filename discovered in Step 1).
- To discover the number of supported GUIDs:
- Send IOCTL - IOCTL_TEEDRIVER_GET_FW_CLIENT_COUNT (via DeviceIoControl())
- Input buffer – None
- Output Buffer – FW_CLIENT_COUNT struct
- Send IOCTL - IOCTL_TEEDRIVER_GET_FW_CLIENT_COUNT (via DeviceIoControl())
- Send a query that will return a list of structures that describes each one of the supported Intel MEI GUIDs. The number of entries in the structure equals the FW_CLIENT_COUNT extracted in Step 3:
- Send IOCTL - IOCTL_TEEDRIVER_GET_FW_CLIENTS (via DeviceIoControl())
- Input Buffer – None
- Output Buffer – Array of FW_CLIENT_EXPANDED structure. The number of entries is equal to FW_CLIENT_COUNT (see the FW_CLIENT_EXPANDED definition).
- Send IOCTL - IOCTL_TEEDRIVER_GET_FW_CLIENTS (via DeviceIoControl())
- For each entry, compare FW_CLIENT_EXPANDED.ProtocolName with the Intel UPID MEI Client GUID (92136C79-5FEA-4CFD-980E-23BE07FA5E9F). If found, the Intel UPID feature is supported.
- In the Intel UPID FW_CLIENT_EXPANDED structure found in Step 5, check the FW_CLIENT_EXPANDED.ProtocolVersion to determine the version of the Intel UPID protocol that the firmware supports.
Definitions:
UPID MEI Command Structure
UPID_HECI_HEADER
Header for Intel UPID commands.
Field Description
| Field Name | Field Type | Description |
|---|---|---|
|
Feature |
UINT8 |
The command feature code. See UPID_COMMAND_FEATURE for feature codes. |
|
Command |
UINT8 |
The command code. See UPID_COMMAND for command codes. |
|
ByteCount |
UINT16 |
Total length, excluding the message header. |
UPID_COMMAND_FEATURE
Command feature codes.
Note: sizeof(enum) is sizeof(UINT32) = 4 bytes.
UPID_COMMAND
Command codes.
Note: sizeof(enum) is sizeof(UINT32) = 4 bytes.
UPID_STATUS
Status codes.
Note: sizeof(enum) is sizeof(UINT32) = 4 bytes.
| Status | Caused By (in Specific Command) |
|---|---|
| UPID_STATUS_FEATURE_NOT_SUPPORTED (Invalid command code) |
|
| UPID_STATUS_INVALID_INPUT_PARAMETER (Input size does not match the expected request size for the specific command) |
UPID_HECI_OEM_PLATFORM_ID_UPDATE
UPID_HECI_OEM_PLATFORM_ID_SIGN
UPID_HECI_OEM_PLATFORM_ID_GET_CERTIFICATE_CHAIN:
|
| UPID_STATUS_INTERNAL_ERROR (Examples: file system error, crypto error) |
|
| UPID_STATUS_NOT_ALLOWED_AFTER_EOP |
UPID_HECI_PLATFORM_ID_FEATURE_STATE_SET
UPID_HECI_PLATFORM_ID_FEATURE_STATE_OS_CONTROL_SET
UPID_HECI_OEM_PLATFORM_ID_UPDATE
UPID_HECI_OEM_PLATFORM_ID_SIGN:
|
| UPID_STATUS_INVALID_STATE |
UPID_HECI_PLATFORM_ID_GET
|
|
UPID_STATUS_NOT_ALLOWED_AFTER_ |
UPID_HECI_OEM_PLATFORM_ID_UPDATE
|
| UPID_STATUS_MAX_COUNTER_EXCEEDED |
UPID_HECI_OEM_PLATFORM_ID_UPDATE
|
| UPID_STATUS_INVALID_STATE |
UPID_HECI_OEM_PLATFORM_ID_SIGN
UPID_HECI_OEM_PLATFORM_ID_GET_CERTIFICATE_CHAIN:
UPID_HECI_PLATFORM_ID_GET
|
| UPID_STATUS_NOT_ALLOWED_AFTER_CBD |
UPID_HECI_OEM_PLATFORM_ID_UPDATE
|
UPID_PLATFORM_ID_FEATURE_SUPPORT_GET
Returns the UPID feature support.
UPID_PLATFORM_ID_FEATURE_SUPPORT_GET Request
| Field Name | Field Type | Description |
|---|---|---|
| Header | UPID_HECI_HEADER | Request header |
UPID_PLATFORM_ID_FEATURE_SUPPORT_GET Response
|
Field Name
|
Field Type
|
Description
|
|---|---|---|
|
Header |
Response header |
|
|
Status |
Status |
|
|
platformIdSupported |
UPID_SUPPORT |
UPID and Attestation support state |
PlatformIdSupported
Note: If a platform supports Intel UPID Attestation, the value of PlatformIdSupported is 3 (i.e., Intel UPID must also be supported on the platform).
UPID_PLATFORM_ID_FEATURE_STATE_GET
Returns the Platform ID feature state.
UPID_PLATFORM_ID_FEATURE_STATE_GET Request
typedef struct { UPID_HECI_HEADER Header; } UPID_PLATFORM_ID_FEATURE_STATE_GET_Request;
|
Field Name
|
Field Value
|
Description
|
|---|---|---|
|
Header |
Request header |
UPID_PLATFORM_ID_FEATURE_STATE_GET Response
|
Field Name
|
Field Value
|
Description
|
|---|---|---|
|
Header |
Response header |
|
| Status | UPID_STATUS | Status |
| FeatureEnabled | UINT8 | Feature state (0/1) |
UPID_PLATFORM_ID_FEATURE_STATE_SET
Sets the Platform ID feature state.
UPID_PLATFORM_ID_FEATURE_STATE_SET Request
|
Field Name
|
Field Value
|
Description
|
|---|---|---|
|
Header |
Request header |
|
|
FeatureEnabled |
UINT8 |
Feature state (0/1) |
UPID_PLATFORM_ID_FEATURE_STATE_SET Response
|
Field Name
|
Field Value
|
Description
|
|---|---|---|
|
Header |
Response header |
|
|
Status |
Status |
UPID_PLATFORM_ID_GET
Returns the Unique Platform ID of the system.
UPID_PLATFORM_ID_GET Request
| Field Name | Value | Description |
|---|---|---|
| Header | UPID_HECI_HEADER | Request header |
UPID_PLATFORM_ID_GET Response
| Field Name | Value | Description |
|---|---|---|
|
Header |
UPID_HECI_HEADER |
Response header |
|
Status |
UPID_STATUS |
Status |
|
PlatformIdType |
OEM Platform ID type |
|
|
OEMPlatformId |
UINT8[32] |
OEM Platform ID |
|
CSMEPlatformId |
UINT8[32] |
Intel CSME Platform ID |
Note: After retrieving the UPID, it is recommended to disable the feature state using UPID_PLATFORM_ID_FEATURE_STATE_SET.
UPID_OEM_PLATFORM_ID_TYPE
UPID presentation type.
Note: sizeof(enum) is sizeof(UINT32) = 4 bytes.
| Item Name | Description |
|---|---|
| UPID_OEM_PLATFORM_ID_TYPE_NOT_SET | OEM Platform ID is not set. |
| UPID_OEM_PLATFORM_ID_TYPE_BINARY | OEM Platform ID includes binary values. |
| UPID_OEM_PLATFORM_ID_TYPE_PRINTABLE_STRING | OEM Platform ID includes printable characters. |
UPID_PLATFORM_ID_SIGN
Signs user data with device key.
UPID_OEM_PLATFORM_ID_SIGN Request
UPID_KEY_IDX
Private key used for signing. Specifies the type of key requested from the firmware, depending on whether
the signing request is coming from an OS application (1) or from the BIOS (0).
Note: sizeof(enum) is sizeof(UINT32) = 4 bytes.
| Field Name | Description |
|---|---|
| KeyIdx |
User key type: 0: BIOS 1: OS |
| DataLen | Actual length of data in the dataToSign buffer |
| DataToSign |
The data that is signed by the Intel CSME key using the ECDSA384_WITH_SHA384 algorithm. DATA_TO_SIGN_MAX_SIZE is 1024 bytes. |
UPID_OEM_PLATFORM_ID_SIGN Response
| Field Name | Description |
|---|---|
| SignatureMechanism |
Signature mechanism used. 0 – ECDSA 384 SHA384 |
| Signature |
Signature over the input "dataToSign". Note: Actual signature size may be smaller than the signature buffer and depends on the algorithm used in SignatureMechanism |
UPID_OEM_PLATFORM_ID_GET_CERTIFICATE_CHAIN
Get the On Die CA certificate chain used for signing user data.
UPID_OEM_PLATFORM_ID_GET_CERTIFICATE_CHAIN Request
| Field name | Description |
|---|---|
| CertIdx | User certificate type. Specifies the type of certificate requested from the firmware, depending on whether the signing request is coming from an OS application (1) or from the BIOS (0). |
Note: sizeof(enum) is sizeof(UINT32) = 4 bytes.
UPID_OEM_PLATFORM_ID_GET_CERTIFICATE_CHAIN Response
| Field name | Description |
|---|---|
| LengthsOfCertificates | This field corresponds to the length of each one of the certificates returned by Certificates field. It returns 4 unit16, each one is the length of corresponding certificate in Certificates |
| CertificateChain |
This is the certificate chain to return in the order from leaf to root. E.g., the first certificate is the MAX_Certs_length is 3200. |
Use Cases
The following table describes main use cases for Intel UPID.
| Use case | To check whether supported, do the following: |
|---|---|
| Read the Intel UPID | Query the Intel MEI driver for the supported Intel MEI Client GUIDs and verify that the UPID GUID is returned. |
| Attest the Intel UPID |
Or
|
Use Case: Read the Intel UPID
To read the Intel UPID from the OS:
- Set the Intel UPID feature state to Enabled. This can be accomplished by one of the following methods:
- BIOS setting
- OS WMI Command (SetUniquePlatformIDFeatureState)
- Intel MEI command: Using the UPID_PLATFORM_ID_FEATURE_STATE_SET command.
2. Read the Intel UPID using the UPID_PLATFORM_ID_GET command.
3. Set the Intel UPID feature state to Disabled using one of the methods in Step 1.
Use Case: Attest the UPID
The following describes the high-level flow for Intel UPID attestation:
- Set the Intel UPID feature state to Enabled. This can be accomplished by one of the following methods:
- BIOS setting
- OS WMI Command (SetUniquePlatformIDFeatureState)
- Intel MEI command: Using the UPID_PLATFORM_ID_FEATURE_STATE_SET command.
- The attestor application sends a challenge request to the Intel CSME firmware via the Intel MEI UPID_OEM_PLATFORM_ID_SIGN command. The Intel CSME application uses its Intel UPID attestation key to sign the challenge and return a signed challenge response.
-
The attestor application obtains the Intel UPID IDevID certificate chain via the UPID_OEM_PLATFORM_ID_GET_CERTIFICATE_CHAIN command.
- The attestor application retrieves the leaf certificate from the first entry in the certificate chain and verifies that this is an Intel UPID attestation certificate by checking that the Extended Key Usage (EKU) field includes the OID 2.16.840.1.113741.1.2.4.6 (for BIOS Intel UPID attestation) or 2.16.840.1.113741.1.2.4.7(for OS Intel UPID attestation).
- If valid, the attestor verifies that this is a Production system Intel CSME certificate chain (and not an Engineering Sample or Debug system or other Intel chipset IP certificate). This is verified by the Issuer Field in the ROM ODCA certificate:
- Find the CSME ROM ODCA Certificate: This is the 4th certificate in the chain with the Subject Field Common Name attribute containing “ROM CA”.
- In the Issuer field, the organizationalUnitName Attribute (OU) must have a prefix equal to either ODCA 2 CSME P or On Die CSME P, where P stands for Production.
- If valid, the attestor application retrieves the public key from the leaf certificate and verifies the challenge response signature. See Verifying the Challenge Response Signature.
- If the challenge response is valid, the attestor verifies the certificate chain up to the Intel iKGF Root CA installed in the service (https://tsci.intel.com/content/OnDieCA/certs/OnDie_CA_RootCA_Certificate.cer), and verifies that no certificate in this chain has been revoked by the iKGF CA CRL.
- If the certificate chain is valid, the attestor application verifies the Intel UPID against the IDevID certificate chain:
- Retrieves the OEM Platform ID from the 520SerialNumber attribute in the Subject field of the IDevID certificate, and verifies it against the first 32 bytes of the Intel UPID.
- Retrieves the hwSerialNum in the SubjectAltName field in the certificate and compares it with the second 32 bytes of the Intel UPID.
- If valid, the attestor application verifies that the first 20 bytes of the hwSerialNum in the SubjectAltName field match the first 20 bytes of the SHA256 hash of the ROM ODCA Certificate (identified in Step 4).
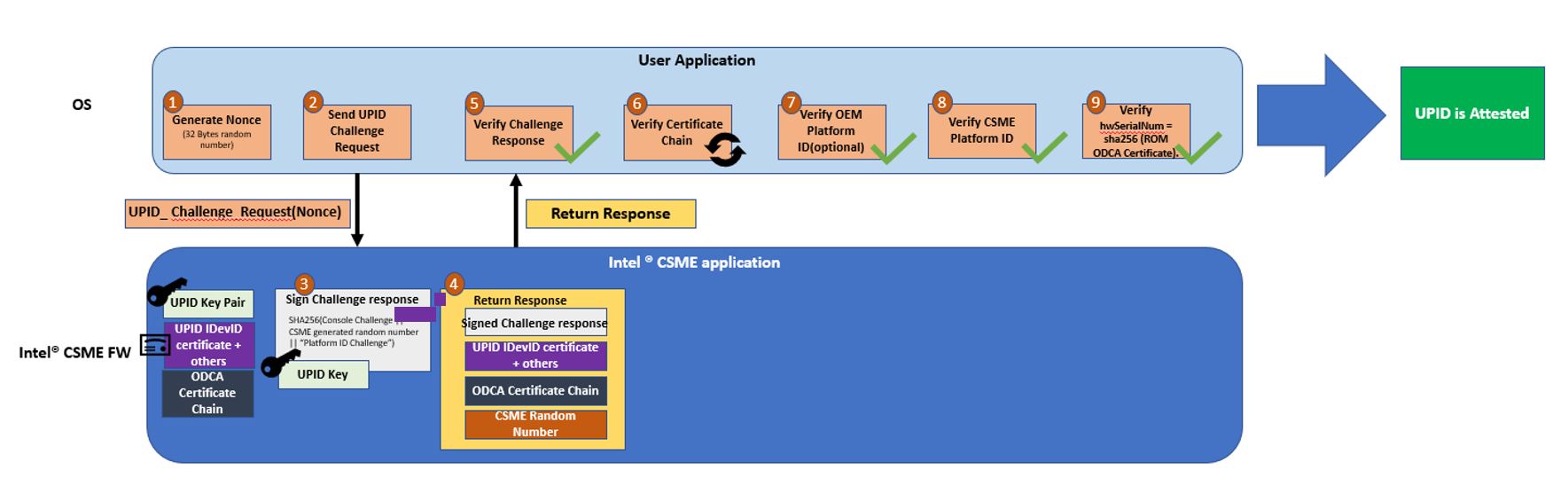
Verifying the Challenge Response Signature
- Decrypt the signature field returned in the challenge response with the public key that resides within the Intel UPID IDevID leaf certificate per the SignatureMechanism parameter in the response.
- Compute the hash of the challenge data in the dataToSign parameter that was sent to CSME FW in UPID_OEM_PLATFORM_ID_SIGN Intel MEI command, per the hash function in SignatureMechanism.
- Compare the decrypt signature field in Step 1 with the hash value in Step 2. Both values should be equal.
Verification Method
Any open-source crypto library that verifies ECDSA signatures can be used for verifying the challenge response signature returned from the Intel CSME firmware.
For example, the Open SSL ECDSA_verify function can be used with the following input parameters:
Method declaration:
Method call:
|
Parameter |
Meaning |
|
Digest |
Hash of the dataToSign |
|
Sig |
The returned signature field in the challenge response transformed to ECDSA_SIG encoding |
|
eckey |
The public key that resides in the IDevID (leaf) certificate returned within the challenge response. Intel® ME eckey curve type is nist p384 |
Verifying the OCDA Certificate Chain
To verify the ODCA certificate chain, the user application is required to check all signatures in the chain and check that the root certificate matches the iKGF root certificate. This can be accomplished by the standard PKI certificate chain verification method, taking the root CA from a trusted Intel site.
If attestation fails due to a signation certification verification error, the Intel UPID certificate should not be trusted.
Intel UPID WMI Provider Commands
WMI is a Windows management subsystem that allows an administrator to access Intel MEI APIs using a standard interface.
Notes:
1. Before you can use WMI commands, you need to ensure that WMI is supported on the system that you are querying.
To determine whether your computer has the Intel CSME WMI provider (which is usually pushed by Microsoft Windows Update), perform one of the following actions:
• Run a WMI command and check whether it succeeds.
• Open a Command window and run sc query. Check whether the Intel(R) Management Engine WMI Provider Registration service is listed.
• Open a PowerShell window and run the Get-Service command. Check whether the Intel(R) Management Engine WMI Provider Registration is listed. This can also be found in the device manager (Software components \ Intel(R) Management Engine WMI Provider).
If your computer is missing the Intel CSME WMI provider, you need to install the Intel CSME Software package, which includes the provider.
The Intel CSME Software package and installation instructions are available from your OEM.
Alternatively, you can download the Intel CSME Software from Intel’s Download Center. See the section Installing Intel® CSME Software Components in the
Intel® Converged Security and Management Engine Software Installation and Configuration Guide included with the software package.
2. The WMI commands must be executed with OS Admin control.
Set Intel UPID Feature State via WMI
To enable the feature state via WMI, open PowerShell and execute:
Invoke-CimMethod -Namespace "root\Intel_ME" -ClassName ME_System -MethodName setUniquePlatformIDFeatureState -Arguments @{ state = $True}
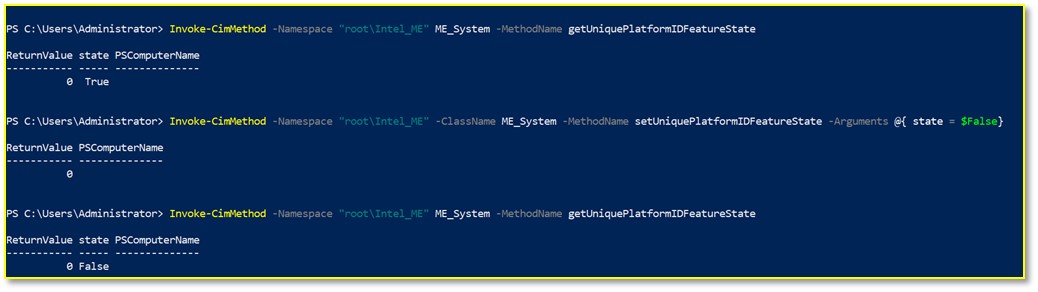
Get Intel UPID Feature State via WMI
To retrieve the feature state, open PowerShell and execute:
Invoke-CimMethod -Namespace "root\Intel_ME" -ClassName ME_System -MethodName getUniquePlatformIDFeatureState
Read Intel UPID via WMI
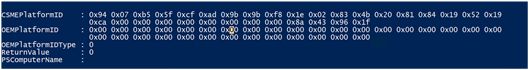
Note: This command is available only when the Intel UPID state has been set to Enabled via the BIOS, WMI or an Intel MEI command.
To read the Intel UPID, open PowerShell and execute:
Invoke-CimMethod -Namespace "root\Intel_ME" -ClassName ME_System -MethodName getUniquePlatformID
The system’s unique identity is displayed in two parts:
- Intel CSME Platform ID
- OEM platform ID. If the ID has not yet been set, this field will be filled with zeros.