Side Channel Vulnerabilities: Microarchitectural Data Sampling and Transactional Asynchronous Abort
Overview
On May 14, 2019, Intel and other industry partners shared details and information about a new group of vulnerabilities collectively called Microarchitectural Data Sampling (MDS).
First identified by Intel’s internal researchers and partners, and independently reported to Intel by external researchers, MDS is a subclass of previously disclosed speculative execution side channel vulnerabilities and is comprised of four related techniques. Under certain conditions, MDS potentially provides a malicious program the means to read data that the program otherwise would not be able to see. MDS techniques are based on sampling data leaked from small structures within the CPU using a locally executed speculative execution side channel. MDS does not, by itself, provide malicious actors the ability to choose which data is leaked using these methods. Practical exploitation of MDS is a very complex undertaking.
Starting with select 8th and 9th Generation Intel® Core™ processors, as well as the 2nd Generation Intel® Xeon® processor Scalable family, MDS is mitigated in hardware. More details can be found here. We expect all future Intel® processors include hardware mitigations addressing these vulnerabilities.
The Transactional Asynchronous Abort (TAA) vulnerability affects the same microarchitectural structures as MDS but uses a different mechanism for the exploit. On CPUs that are vulnerable to MDS, the existing MDS mitigation helps address the TAA CVE vulnerability. On CPUs that are not vulnerable to MDS but have transactional functionality, additional mitigation might be required. Additional details can be found here.
Mitigation
For products where MDS or TAA is not addressed in hardware, Intel is releasing processor microcode updates (MCU) as part of our regular update process with OEMs. These are coupled with corresponding updates to operating system and hypervisor software.
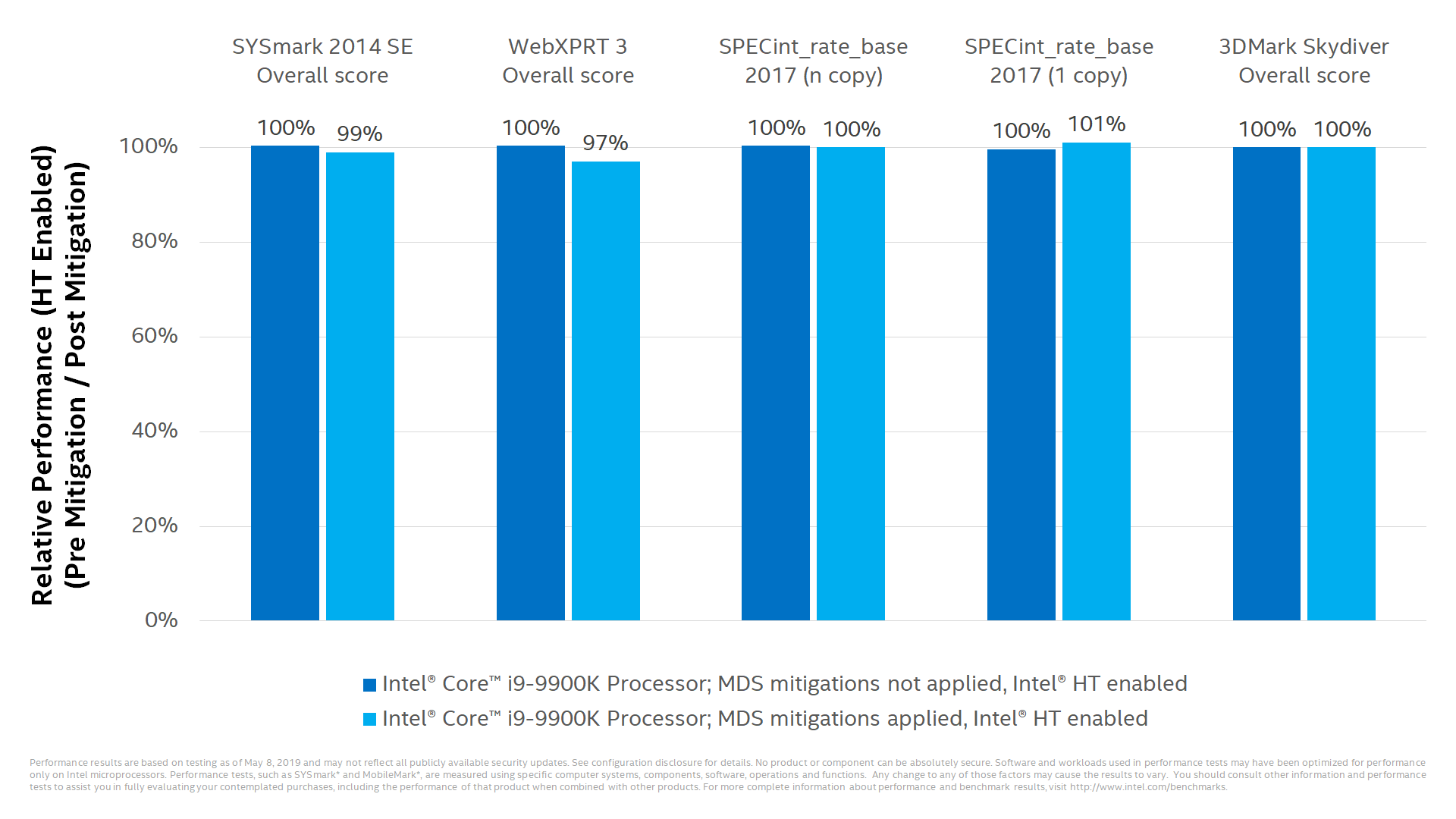
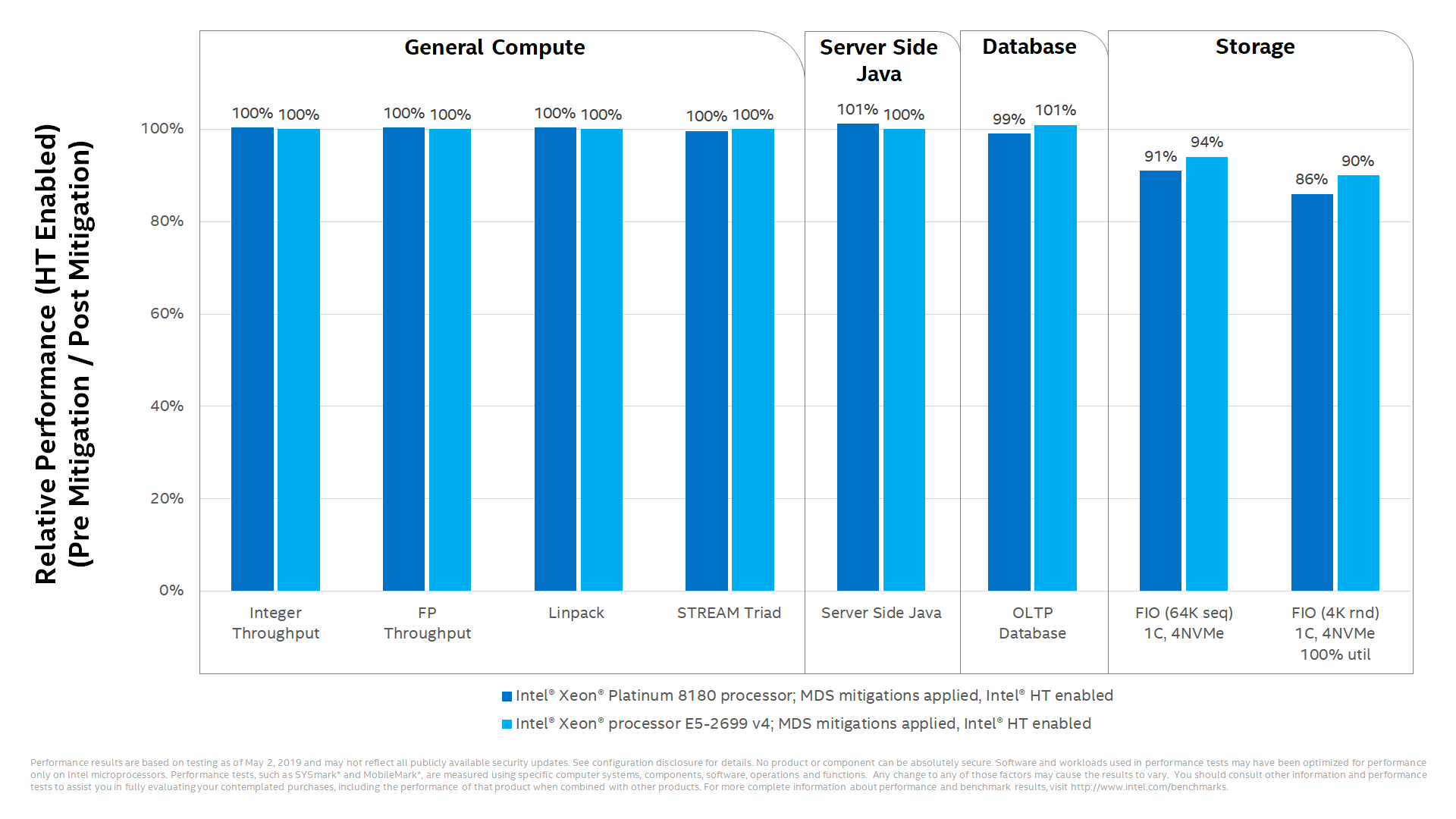
When these mitigations are enabled, minimal performance impacts are expected for the majority of PC client application based benchmarks. Performance or resource utilization on some data center workloads may be affected and may vary accordingly.
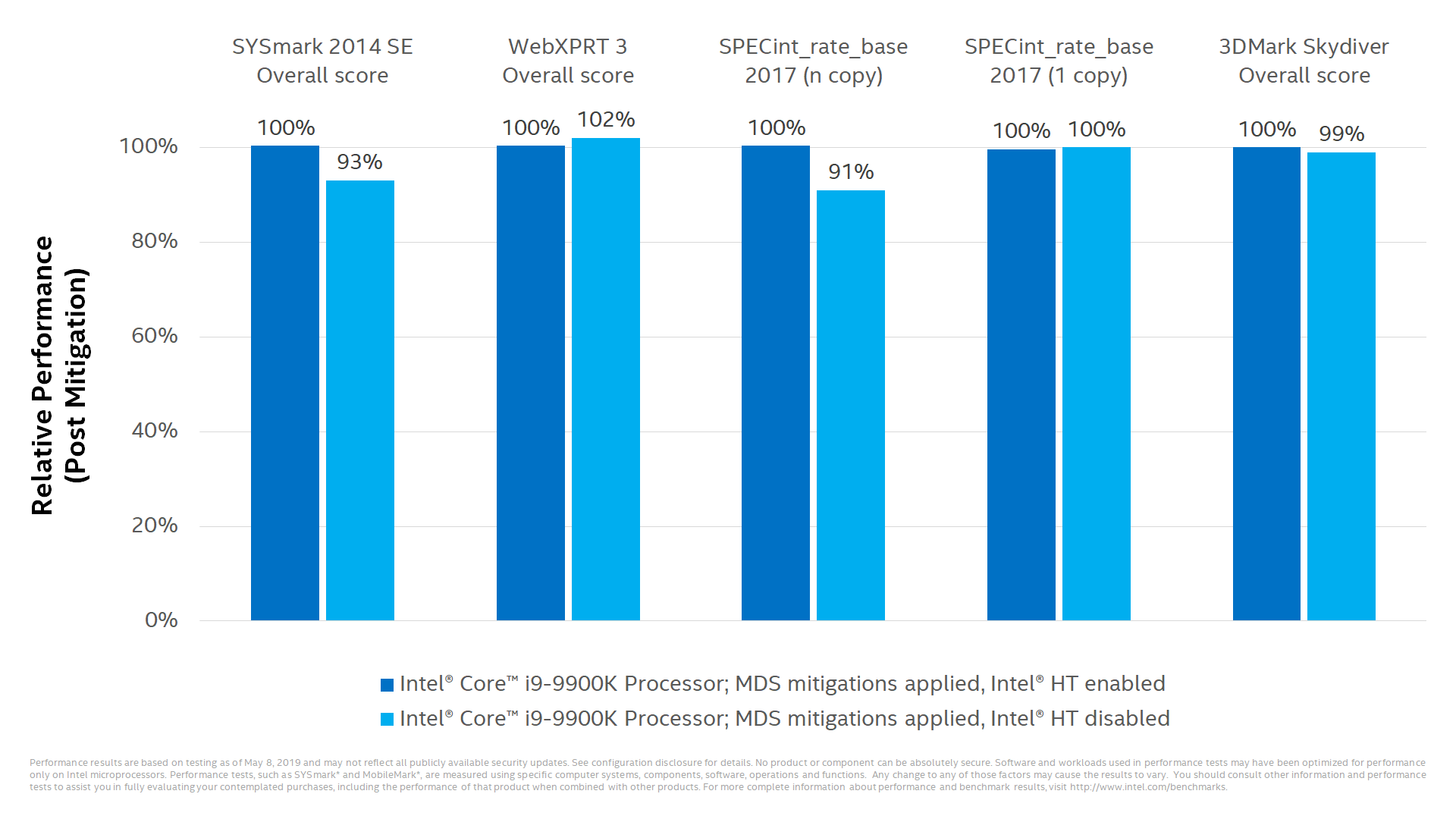
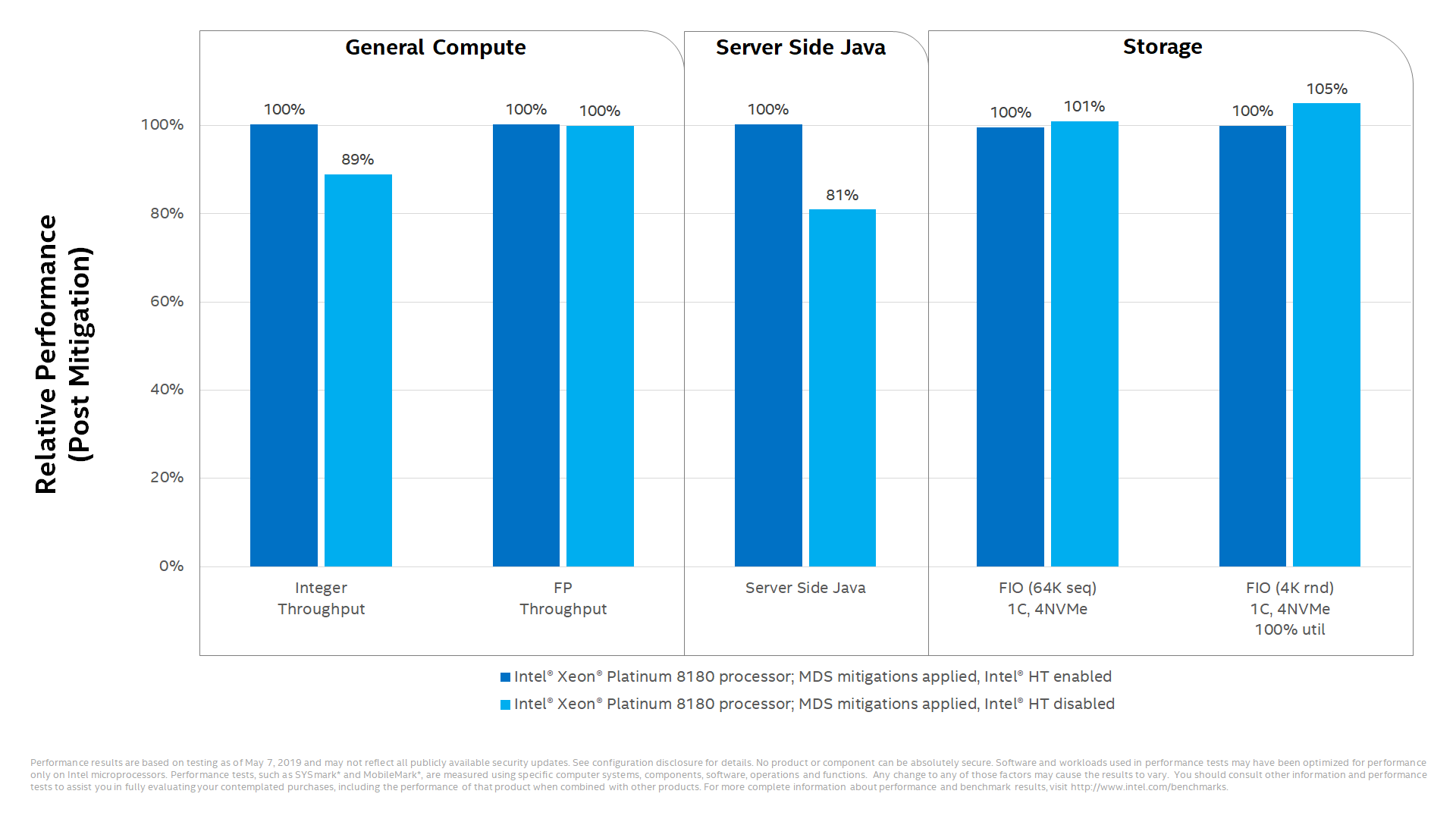
Once these updates are applied, it may be appropriate for some customers to consider additional steps. This includes customers who cannot guarantee that trusted software is running on their system(s) and are using Simultaneous Multi-Threading (SMT). In these cases, customers should consider how they utilize SMT for their particular workload(s), guidance from their OS and VMM software providers, and the security threat model for their particular environment. Because these factors will vary considerably by customer, Intel is not recommending that Intel® HT be disabled, and it’s important to understand that doing so does not alone provide protection against MDS.
More detailed information on mitigations affecting MDS vulnerabilities can be found here.
Limited Performance Impact for the Majority of PC Clients
Performance Impacts for PC Clients with Intel® Hyper-Threading Disabled
Performance Impacts on Select Data Center Workloads
Performance Impacts on Select Data Center Workloads with Intel® HT Disabled
- Processor: Intel® Core™ i9-9900K processor
- Memory: 2x16GB
- Storage: Intel® 760p 512GB SSD NVMe*
- Display Resolution: 1920x1080
- OS: Windows* 10, version 1809
- Graphics: Intel® HD Graphics 630
- Date Tested: May 7, 2019
- Tested By: Intel Corporation. Note: All the Client measurements used the same SKUs. For MDS impact, changed only microcode and OS for various configurations
- SPEC benchmark results based on Intel internal measurements; ratios provided as research usage
- Processor: 1-node, 2x Intel® Xeon® Platinum 8180 processor (28 core, 2.5 GHz) on S2600WFT platform
- Memory: 384 GB (12 slots / 32GB / DDR4-2666) total memory
- Storage: S3710 400G
- Pre MDS mitigation:
- OS: Redhat Enterprise Linux* 7.6 3.10.0-957.10.1.el7.x86_64
- Microcode: 0x200005a
- Post MDS Mitigation:
- OS: Redhat Enterprise Linux* 7.63.10.0-957.12.2.el7.x86_64
- Microcode: 0x200005e
- Processor: 1-node, 2x Intel® Xeon® processor E5-2699 v4 (22 core, 2.2 GHz) on S2600WTTS1R platform
- Memory: 256 GB (8 slots / 32GB / DDR4-2666 (run at 2400)) total memory
- Storage: S3710 400G
- Pre MDS mitigation:
- OS: Redhat Enterprise Linux* 7.6 3.10.0-957.10.1.el7.x86_64
- Microcode: 0xb000030
- Post MDS Mitigation:
- OS: Redhat Enterprise Linux* 7.6 3.10.0-957.12.2.el7.x86_64
- Microcode: 0xb000036
Assessing Risk
Exploiting the MDS vulnerabilities outside the controlled conditions of a research environment is a complex undertaking. MDS vulnerabilities have been classified as low to medium severity per the industry standard CVSS, and it’s important to note that there are no reports of any real world exploits of these vulnerabilities.
As technologies become more and more complex, we believe it takes the ecosystem working together to keep products and data more secure. We appreciate the research community and our industry partners for their contributions and coordinated disclosure of these issues.
Resources
System manufacturers, operating system vendors, and others not listed here may have published information regarding this situation. You should check for updates or advisories from your system manufacturer or operating system vendor. This list is not comprehensive.
Resource from Intel
Resources from OS and Hardware Vendors
Third-party Information on Sound Security Practices
Information from System Manufacturers
Intel Customer Support
For Assistance Contact Your Operating System or System Manufacturer Above, or Intel Customer Support
Frequently Asked Questions
Transactional Asynchronous Abort (TAA)(CVE-2019-11135) is a speculative execution side channel issue related to Intel® Transactional Synchronization Extensions (Intel® TSX). TAA affects the same microarchitectural structures as microarchitectural data sampling (MDS). Intel continues to work with industry partners to develop and disclose information and mitigations for TAA.
MDS is a sub-class of previously disclosed speculative execution side channel vulnerabilities and is comprised of four closely related CVEs first identified by Intel’s internal researchers and partners and independently reported to Intel by external researchers.
- Microarchitectural Load Port Data Sampling (MLPDS) - CVE-2018-12127
- Microarchitectural Store Buffer Data Sampling (MSBDS) - CVE-2018-12126
- Microarchitectural Fill Buffer Data Sampling (MFBDS) - CVE-2018-12130
- Microarchitectural Data Sampling Uncacheable Sampling (MDSUM) - CVE-2019-11091
Exploiting MDS and TAA outside the controlled conditions of a research environment is a complex undertaking and Intel is not aware of any reported real-world usage of these security issues. The microcode updates Intel has released, when coupled with corresponding updates to operating system and hypervisor software available from our industry partners, provide many customers with the protections they need. It may be appropriate for some customers to consider additional steps. This includes customers who cannot guarantee that trusted software is running on their system(s) and are using Simultaneous Multi-Threading (SMT). In these cases, customers should consider how they utilize SMT for their particular workload(s), guidance from their OS and VMM software providers, and the security threat model for their particular environment. In all cases, Intel recommends that people keep their systems up to date.
Yes. Processor microcode released as part of Intel’s regular update process, when coupled with operating system and hypervisor software updates available from our industry partners, helps ensure consumers, IT professionals, and cloud service providers have access to the protections they need.
For in-depth information, visit our Software Security website.
There are three cases depending on which mitigation path the user chooses:
a. No mitigation chosen. No performance impact.
b. Disable TSX
- Applications that do not use TSX are unaffected
- TSX enabled applications will have all transactions aborted. Impact depends on how heavily TSX is used and how much the application performance depends on TSX transactions committing in parallel.
c. Use VERW to overwrite microarchitectural buffers. On systems that already use MDS mitigation there is no additional impact. On systems that don’t use MDS mitigation currently this will be similar impact as MDS mitigations.
No. Intel is not aware of any reported real-world usage of these vulnerabilities.
Yes. MDS vulnerabilities are addressed by hardware changes with select 8th and 9th Generation Intel® Core™ processors, as well as the 2nd Generation Intel® Xeon® processor Scalable family. We expect all future processors will include hardware mitigations addressing these vulnerabilities.
More information can be found by going here.
No. Intel is not recommending that users disable Intel® Hyper-Threading Technology (Intel® HT Technology). It’s important to understand that doing so does not alone provide protection against MDS, and may impact workload performance or resource utilization that can vary depending on the workload.
Coordinated Vulnerability Disclosure (also referred to as "CVD" or “responsible disclosure”) is widely regarded as the best way to responsibly protect customers from security vulnerabilities. CVD is based on two foundational concepts: when companies become aware of security vulnerabilities, (1) they work quickly, collaboratively, and effectively to mitigate those vulnerabilities, and (2) they simultaneously take steps to minimize the risk that exploitable information becomes available before mitigations are available – through leaks or otherwise – to those who would use it for malicious purposes.
These principles are perhaps best expressed by the Computer Emergency Response Team (CERT) at Carnegie Mellon’s Software Engineering Institute:
“The public and especially users of vulnerable products deserve to be informed about issues with those products and how the vendor handles those issues. At the same time, disclosing such information without review and mitigation only opens the public up to exploitation. The ideal scenario occurs when everyone coordinates and cooperates to protect the public.”
More information on coordinated disclosure and its importance can be found in the Guide to Coordinated Vulnerability Disclosure.
Impacted Intel Platforms
Please check with your system vendor or equipment manufacturer (see links above) for more information regarding your system.
Learn more details on microcode updates Intel is releasing to address MDS and TAA.
More information can be found on Intel’s security advisories for MDS and TAA.